Virtual Sitting Ducks &
How Not to be One
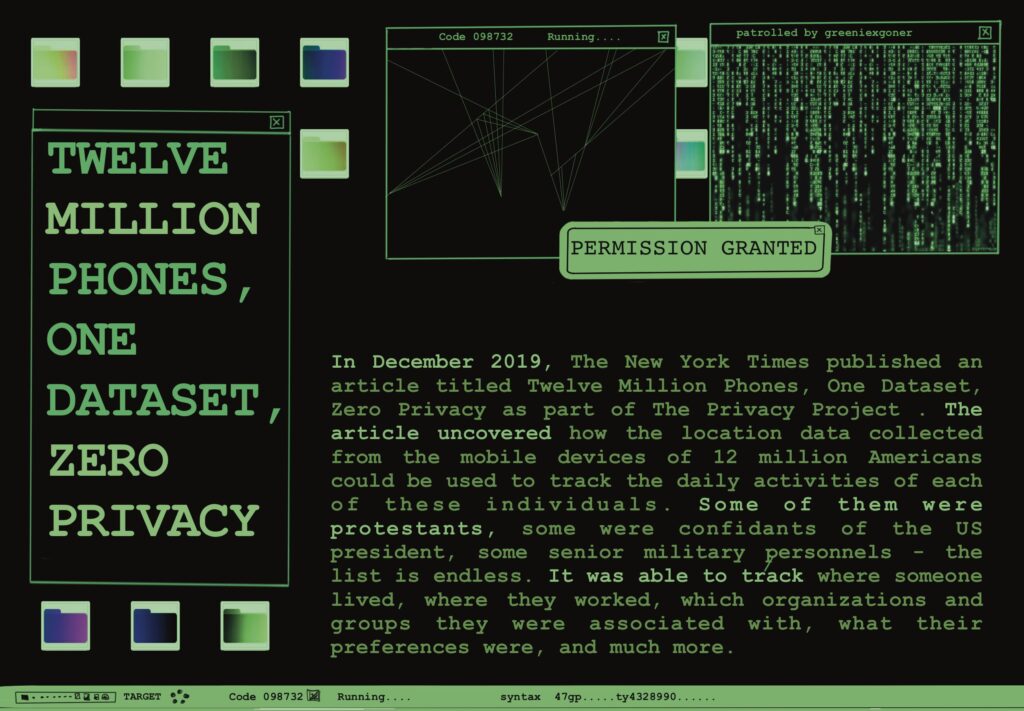
Yes, these could be used to feed extremely relevant ads to the general person; but imagine what the same data could be used for when it comes to significant personnel, victims of abuse, intelligence officers, politicians, public figures, celebrities, and so on. In an era where your data can be used against you just as brutally as it could be used to make your life simpler and better, here is an article introducing the barebones of what you need to know about it.
The spectrum of the online world is way wider than the tiny portion most of us expose ourselves to and are familiar with. Even those of us most active on the web are often oblivious to the lurking dangers thereof. Sometimes even someone who is perfectly aware of the dangers is lured by the appealing user-interfaces modern websites and applications consist of. Critical personal information that you would hesitate to share with even your closest confidants are accessible relatively easily to strangers with malicious intents. Sounds scary? Things get even scarier if you’re unaware of the things that can go wrong if you don’t take your online security seriously.
Privacy, Anonymity, and Confidentiality
There are, loosely, three types of online breaches – privacy, anonymity, and confidentiality. The implications of privacy and anonymity are often confused so let’s clear that up first. Privacy is the attribute of having control over the flow of your information – which is basically anything you input in apps or websites and some metadata (technical stats about your device and the inferences that can be deduced from them). The extent of the control is a matter of consent and agreement between the user and the service-provider (the website or the application you’re using), but whatever that extent is must be clearly explained to the user. Which isn’t the case in pretty much all cases1 otherwise it wouldn’t make much sense to write this article. Loose laws – and in some cases no laws at all – regarding the protection of online privacy of the user allows for such fuzzy lines of legality and illegality when it comes to the collection of data.2 Privacy also indirectly assures that critical information will not be collected and the user can opt-out at any time.
Anonymity, on the other hand, is the attribute of not being uniquely identified online in a persistent way. By “a persistent way” I mean something like this – a website may have features that personalize your experience (any preferences you change from the settings of the site and/or anything that you can compare when viewing the same website from a different device or account and find differences) for the duration of your browsing session but the inputs that were used to personalize your experience shouldn’t persist the next time you visit the same website. Yes, it would make the user experience much smoother and better if preferences like that did persist, but that’s where the trade-off of anonymity comes in.
Confidentiality, on the other hand is the attribute of data-collection, also according to what the user permits (which, again, isn’t the case most of the time), but this time it can be critical information. The service provider, however, promises, in this case, to treat the user-data with utmost protection so that it doesn’t end up in the wrong hands and that it is not used for purposes other than what the user consented to.
You Can Run but You Can’t Hide
Websites track you all the time. Whether you’re consistently visiting a certain website or not, just visiting a website once can enable it to track you pretty much all over the internet.3 You can be profiled to be fed personalized ads solely for the purpose of marketing benefits. But what’s wrong with seeing a lot of ads? Isn’t it good to be advertised with things that you would want to buy? Perhaps some would agree; in fact, I’d be one of them. However, advertisements are not the only purpose your information can be used for. They can, and probably are, used for rather unsettling purposes by tech-giants, organizations in authority, and possibly for even more horrifying purposes if it reaches the hands of malicious hackers.
The question of “what purposes” goes beyond the scope of this article. The worst part is that a lot of this information can be, and is collected without the users’ consent. However, the line between the information which is legal to collect and that which is not is rather fuzzy; this allows marketers to work around the barely existing privacy and anonymity protective measures and get their hands on sensitive information regardless. Confidentiality breaches can occur either when a company chooses to abuse its user-data or there occurs a data-breach in the company (which are more frequent than what is publicly reported). Although neither is preferable, the latter is worse in the sense that your data can not only end up in malicious hands but now it may be used to blackmail you and/or put you in all sorts of trouble. The former, on the other hand, usually goes as far as showing you unsettlingly personal ads (that isn’t to say that it can’t be used for more).
Okay, that sounded all grim and gloomy. What can we do about it? Well, you have to take immersive courses in information security, cyber security, networking, ethical hacking, and.. well, the list actually goes on. But this sounds unreal. That’s because it is. No one can fully secure themselves from a directly targeted attack from a sufficiently powerful attacker. It’s not even possible in principle. But there is no reason for you to be so ferociously targeted by cyber criminals or authorities unless you’ve been involved with some really dirty business, in which case you’d already know what to do and you won’t be reading this article that barely touches the surface of defending specifically targeted cyber attacks.
How Not to be The-Average-Joe
But as a regular person, there are a few relatively simple measures you could take. Attacks can be either targeted or untargeted. If you are a targeted victim of cyber attack and you don’t know what to do, this means your attacker is a cyber criminal. In which case, you’ll have to reach out to authorities as soon as you can or else things can get really, really bad.
An untargeted attack (which can be pretty brutal as well), on the other hand, can be easily defended if prepared beforehand.
Any website you visit immediately has access to your IP address which, if you don’t know already, can be used to track down your physical location without dropping a sweat. It’s not even illegal and is baked directly into the backend frameworks used to build websites. To mask your personal IP, you can use VPNs (given that the use of VPNs isn’t illegal in your country/state). How exactly VPNs work is not within the scope of this article to explain. But all VPNs aren’t good and can be just as abusive as a malicious attacker if the VPN provider wanted to. I’ll come to choosing the right one in a bit.
When signing up on a website, if there’s an option to sign-up with google, facebook, apple-id, twitter, github, and similar tech-giants, go for that. This is because you don’t know for sure if the website you’re signing up on encrypts your password and username before storing it in their database. Signing up with one of your accounts that are in the custody of a tech-giant is a safe call because such companies are less likely to falter when it comes to data-protection. Whether they abuse your data or not is a different matter. It’s better to be shown alarmingly personal ads than losing your username and password (which you’ve probably used in at least a hundred different places) to the hands of malicious attackers. It’s kind of like the lesser evil.
Speaking about passwords, don’t use the same password everywhere. If you have trouble remembering a thousand different passwords like any human being who has more important things to do in life than remembering passwords all the time, use password managers. Create long and gibberish passwords that look something like this – ;hdfjgh9598725*(^%^*jKJH (yes I pressed random keys on my keyboard with my eyes closed, don’t judge) or just let your password manager create a random, long, and gibberish password for you everytime you create a new account or something that requires a password. But how do you know that the password managers don’t compromise your data? I’ll come to choosing a reliable password manager in a bit too.
Alright, you sign up with your google account or similar accounts, on websites that you don’t trust. But what if your tech-giant protected account gets compromised? Well, if it’s already compromised, there are steps you can take which are beyond the scope of this article. If they aren’t compromised yet and you wouldn’t like them to be, then use a very strong password for them (password manager!) and use multi-layer authentication (aka. Two-factor authentication) if available.
To prevent websites from persistently snooping on you, use browsers like Mozilla Firefox; or if you’re too paranoid or have enough technical knowledge to handle the learning curve, use Tor. Firefox needs some tweaking before it’s ready to browse the web without being tracked across sites, but Tor comes pre-configured for anonymity. But there’s a principal to follow when browsing the web anonymously. NEVER EVER PROVIDE A PIECE OF INFORMATION ONLINE THAT CAN BE USED TO UNIQUELY IDENTIFY YOU! And also of similar significance, never search for something or visit a website anonymously and then immediately (or simulteneously) search for the same thing or visit the same website un-anonymously, and vice-versa. Modern search engines are good enough to pick up on those two separate actions and put them together to generate a user-profile that can monitor even your anonymous web surfing. How exactly Tor (stands for The Onion Router) and onion routing works is beyond the scope of this article. Speaking of search engines, use DuckDuckGo instead of Google. Yes, google is better in certain use-cases (you’d know it if your use case is one of those), but DuckDuckGo is more than sufficient for the general user.
Location information is another thing that you should consider not sharing at all. Although you don’t have much control over what metadata your mobile device shares with the so-called trusted applications when it comes to android and ios, it never hurts to turn off all location permissions by hand. It might cause you plenty of inconvenience using applications that require location-access to function properly, but I would argue such inconvenience is worth it when it comes to not exposing all your daily activities to location-data collecting companies. You don’t have to deprive yourself of maps entirely, there are open source maps available both on the appstore and playstore which offer plenty of navigation facilities offered by your usual maps application.
Choosing Your Weapons
Well, these aren’t really weapons in any form but it sure sounds cool to call them that. Now, how do you choose a trustworthy VPN, a reliable password manager, a private messenger to chat with your friends and loved ones, a cloud storage, an online workspace manager, an encrypted email service, a file encryptor, and almost anything that handles your critical information?
The immediate no brainer answer – use open source. If you don’t know what open source is, it’s basically a service with its source code available for anyone to have a look at and make changes to. Wait what? Anyone can change it? Doesn’t that make it all-the-more insecure? No. Well, not after a major version of it is deployed into production. See, just like there are bad-coders trying to figure out loop-holes in the system to abuse, there are also good-coders who’re looking to find the same loop-holes and patch them up. Why? Because their privacy relies on the same system as yours does. And for every bad-coder, there are more good-coders than you could think of. That’s why it’s very unlikely to find a security issue in an open source software. And even if an issue does arise, it’s more than likely to be fixed almost immediately as it’s spotted. In short, open source software is always monitored to make sure it’s as impenetrable as possible, and because its source code is public, you can be sure that it can’t have anything that abuses the user’s information because the integrity of the information of the creators and contributors of the software also depend on it being not abusive of its user-information.
References
- Jegatheesan, Sowmyan. (2013). Cookies Invading Our Privacy for Marketing Advertising and Security Issues. 4
- Barth, S., de Jong, M. D. T., Junger, M., Hartel, P. H., & Roppelt, J. C. (2019). Putting the privacy paradox to the test: Online privacy and security behaviors among users with technical knowledge, privacy awareness, and financial resources. Telematics and Informatics. https://doi.org/10.1016/j.tele.2019.03.003
- Cross-site tracking: Let’s unpack that | The Firefox Frontier. (n.d.). Retrieved March 8, 2021, from https://blog.mozilla.org/firefox/cross-site-tracking-lets-unpack-that
Further Reading Resources
- The Beginner’s Guide to VPNs | lifehacker
- How Tor works | The Tor Project
- How DuckDuckGo Works | DuckDuckGo – Privacy
Copyright © 2021 Warisul Imam
About the Author
Waris is a highschool senior, bookworm and writer. His interests include Islamic theology, particle physics, cosmology, maths, and computer science. His writings have been published on blogs like The Ascent, The Nonconformist and Deen Over Dunya. Currently, he’s working on a number of writing projects on a variety of topics ranging from the seerah to physics. Most notably though, he’s known for his peculiar habit of scribbling down equations and solving them whenever he finds himself unoccupied.
Links: Goodreads | Twitter